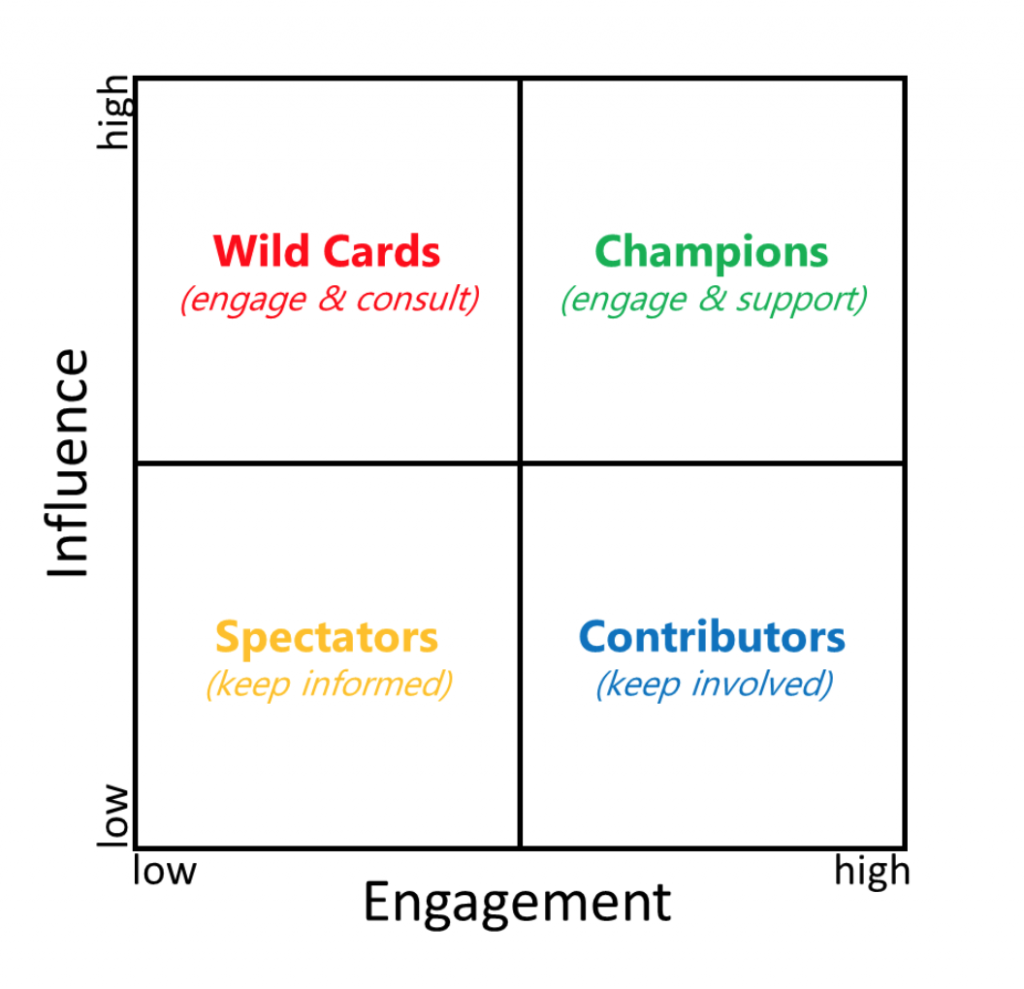
Identity & Access Management: Project Challenges and Recovery #GeekWeek2017
ISACA’s 10th Annual Geek Week Conference in Atlanta, GA featured speakers across a wide range of security topics from Risk Management to Penetration Testing. During the conference, policy and technical tracks provided a forum for participants to exchange experiences from the front lines of IT security, including industry best practices as well as driving both […]
Identity & Access Management: Project Challenges and Recovery #GeekWeek2017 Read More »