Using Systems Thinking to Handle Errors In Your IAM Solution
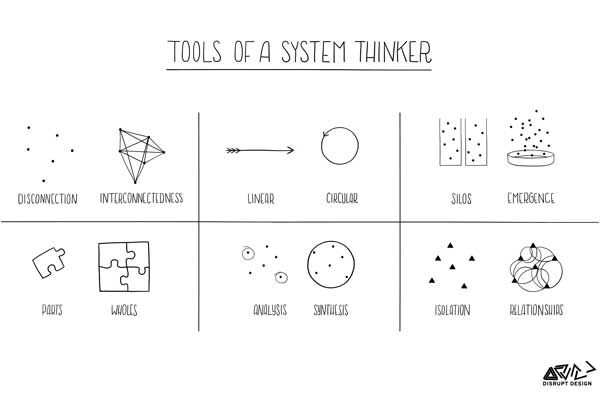
Working in the trenches in HR and IAM operations, it is very easy to lose sight of the big picture. When dealing with events on a daily basis, every event and decision is usually assessed individually, only weighing its immediate effects. This often leads to losing sight of the relationships between process improvement work and […]
Using Systems Thinking to Handle Errors In Your IAM Solution Read More »