Mini Case Study: Getting a Handle on User Data
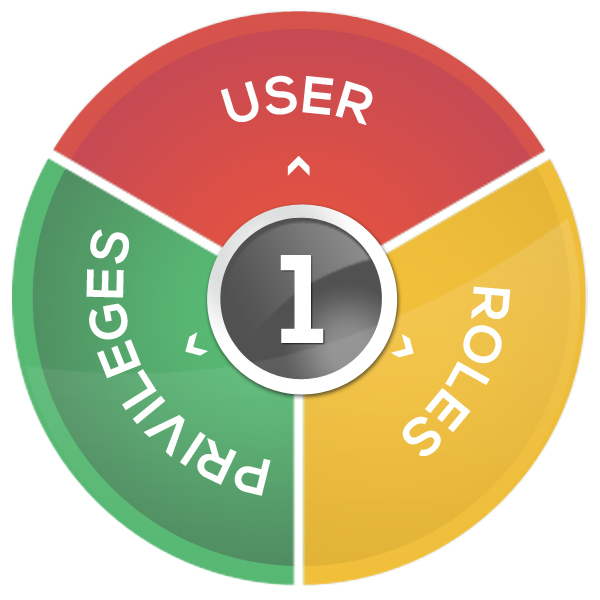
Nicole Keaton Hart and Hanno Ekdahl share a mini case study on the importance of establishing a system of record to maintain user data quality. Identity Management (IAM) is built around the concept of a system of record and establishing a “Gold Standard” data set for each user that is: 1) accurate, 2) actively […]
Mini Case Study: Getting a Handle on User Data Read More »