Let’s take a look at our most popular Identity Management resources and articles from 2020, in no particular order.

Wow, 2020 was quite the year. Cybercrime skyrocketed 600% due to the Covid-19 pandemic and health systems become an even more popular target for hackers. Ransomware attacks doubled in Q3 of 2020 and we saw the first death as a result of a malware cyberattack on a hospital system in Germany. Business email compromise (BEC) saw a sharp rise with over 17% of attacks involving invoice or payment fraud. In fact, $2.3M was stolen from the Wisconsin GOP using BEC.
According to ISACA’s State of Cybersecurity 2020 report, social engineering is the most popular method of attack, with 15 percent of compromised respondents saying it was the method used as a vehicle of entry.
Top 10 Identity Management Resources and Articles from 2020
[Article] Best Practices for Role Based Access Control (RBAC)
RBAC is best suited for organizations that have a mature Identity Governance and Administration (IGA) solution in place. Well-defined user management processes with well-maintained user data are vital pre-requisites to successful implementation because IGA and RBAC are rules-based systems, and those rules will not deliver the expected results if the underlying user data is bad: Garbage data goes in, garbage access comes out!
[Webinar] Preventing Business Email Compromise
In 2019, Victims of Business Email Compromise scams reported $1.78 billion in losses to the FBI’s Internet Crime Complaint Center. Learn more about this threat from Derek Johnson Director, Security from OnSolve, and how to protect yourself and your organization from business email compromise.
[Case Study] FPS Forges New Defenses with Cybersecurity Assessment
As part of the Cybersecurity Assessment, Idenhaus reviewed FPS’s processes and technology to develop recommendations to mature its security program. Our process delivered a clear understanding of FPS’s strengths and struggles and laid out the roadmap to move forward.
[Video] Data Security Takeaways From FTC v LabMD
Michael Daugherty is the Founder of The Cyber Education Foundation and sits on the Idenhaus Board. As the CEO of LabMD, a cancer testing laboratory, he has spent most of the last decade defending his company against charges that it had deficient cybersecurity practices.
[Article] 8 Benefits of an Identity & Access Management Roadmap
Creating an Identity & Access Management (IAM) roadmap is an important first step in helping your organization reap the full benefits of its IAM investment, as well as driving organizational understanding and support. Here are 8 benefits of developing an Identity & Access Management Roadmap before beginning an IAM implementation.
[Webinar] Learning about Policy Based Access Control (PBAC)
Policy Based Access Control (PBAC) offers an advanced framework to centrally manage permissions and provide assurance for the enterprise in a scalable solution. The first step in maturing your IAM program is assessing your needs and identifying the scenarios where PBAC can help automate risk mitigation.
[Article] Five Identity Governance Best Practices
Implementing Identity Governance presents a variety of initiatives and choices, and these projects tend to have similar pitfalls and problems. Over time, lessons learned have become the benchmark for success. Applying best practice means learning from the experience of others to implement your Identity Governance core processes.
[Video] Developing an IAM Roadmap Sets you on the Path to Success
While many organizations do a good job of laying out their technical requirements, too often they fail to link their implementations to business outcomes and fail to build the right IAM foundation to solve the organization’s most pressing business problems.
[Webinar] Which Comes First: Identity Automation or Governance?
Identity Management is key to ensure employees are both empowered to deliver value and prevent damage to the business’s reputation, security, or bottom line. When getting started with IAM, companies will need to decide whether to begin with automation or governance first. This webinar will explore both approaches and make a case for which should come first.
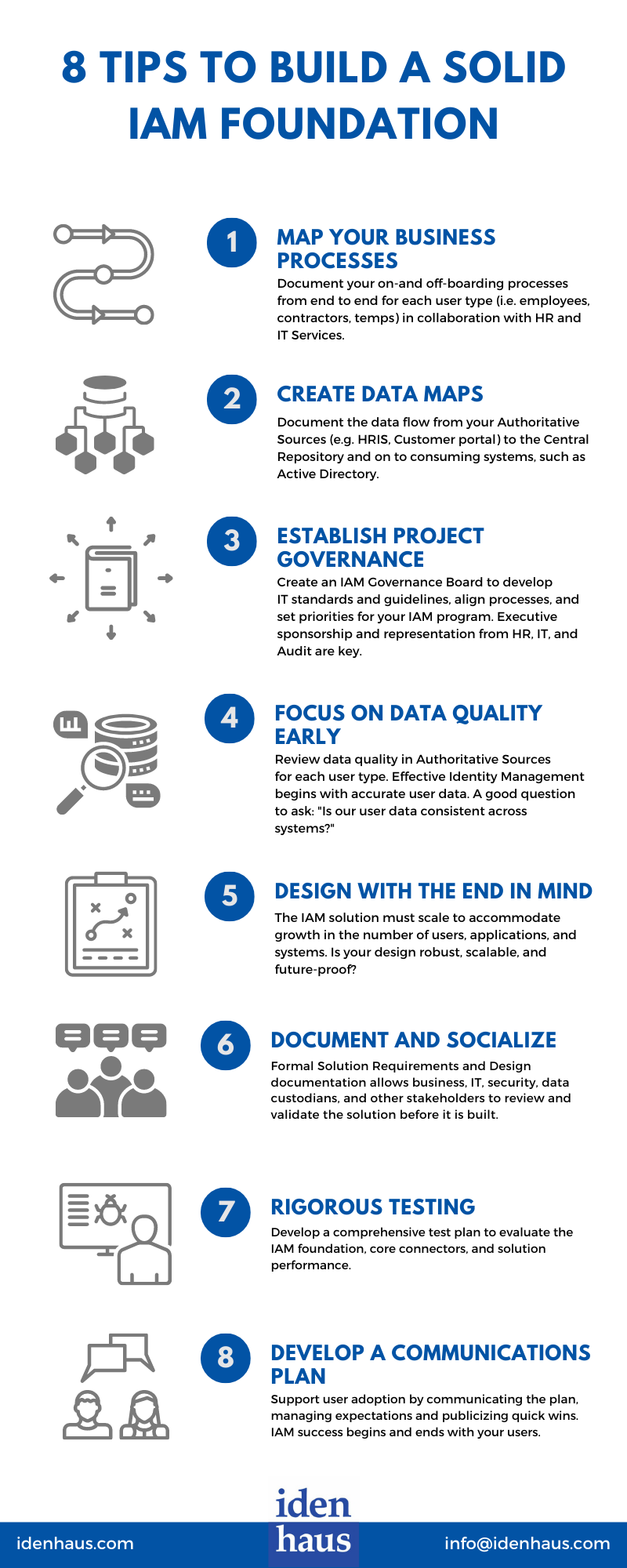
[Infographic] 8 Tips to Build a Solid IAM Foundation
To receive the top identity management resources and articles in your inbox every two weeks (Tuesdays 8 PM EST), subscribe to our Identity Management biweekly and/or our Healthcare Cybersecurity and IAM Digest.
Follow @Idenhaus on Twitter and subscribe to our YouTube channel.
By going to work quickly to solve the most challenging cybersecurity and identity management problems, Idenhaus takes the pain out of securing corporate information and assets for companies that aspire to maximize their potential in this digital age. Click here to contact us







