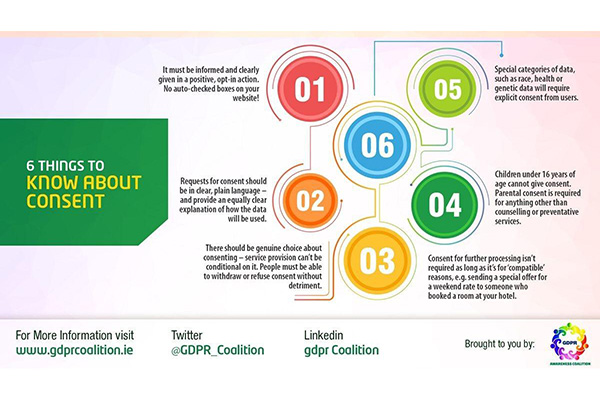
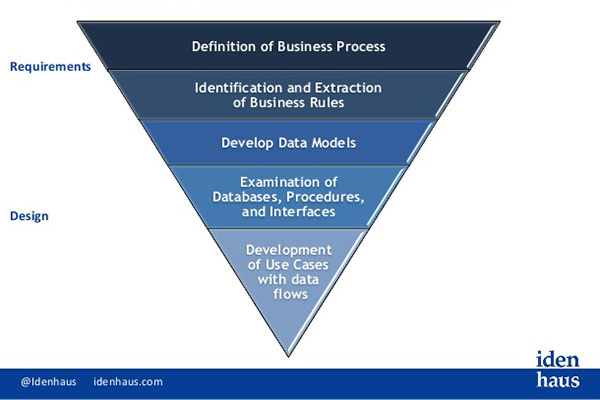
8 Must-Read Identity Management & Cybersecurity Articles, April 2018
Stay informed with the Idenhaus Consulting Identity & Access Management digest. We curate the best IAM/IDM, IoT, Identity Governance/Federation, & Cyber Security articles to help you navigate the ever-changing IT landscape. Subscribe to our biweekly newsletter here. Here are the 8 must-read articles from the first part of April 2018. Enjoy! Identity & Access Management: Project Challenges and Recovery [WEBINAR] This […]
8 Must-Read Identity Management & Cybersecurity Articles, April 2018 Read More »