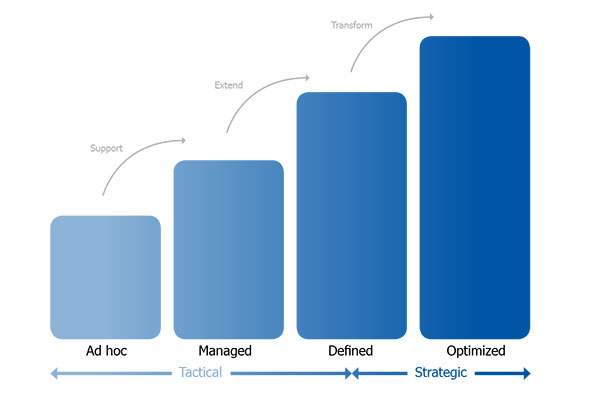
What’s the Big Idea: Identity Management Projects that Deliver
What’s the Big Idea: Identity Management Projects that Deliver By Hanno Ekdahl In the intricate tapestry of modern business, Identity Management (IDM) emerges as a critical thread, weaving together security, efficiency, and user experience. Identity management projects are not mere technical endeavors; they are strategic initiatives that demand a harmonious blend of design, technology, and […]
What’s the Big Idea: Identity Management Projects that Deliver Read More »