
The COVID-19 pandemic and its accompanying business challenges have only accelerated the move to the Cloud. Cybercrime has also accelerated and there are ways to mitigate risks with Identity at their core. We had the opportunity to attend SANS BIPOC in Cybersecurity Forum: Cloud Security conference in February and particularly enjoyed Shinesa Cambric’s talk on Identity-In-Depth: Leveraging Native Tools and a Multi-Layered Approach to Secure Cloud Identity. This session laid out the tools at our disposal to provide additional authentication factors and policy decisions based on identities and the IAM solution deployed. As organizations implement more defenses, they introduce new factors of authentication and improve their Identity in Depth.
[feature_box style=”10″ only_advanced=”There%20are%20no%20title%20options%20for%20the%20choosen%20style” alignment=”center”]
Before you continue reading, how about following us on LinkedIn?
[/feature_box]
When we think of the term “Identity” we usually think of a person and the attributes that describe that user (name, department, workertype, etc.). But in the Information Security domain Identity means much more. The value of an identity is really about understanding the relationships that the user has with the organization’s systems including the level of privileges granted to that individual. Identity is the fundamental element in security since it is a prerequisite for accessing any application/server/service. In this article, we discuss the components of Identity-in-Depth, what happens when an identity is compromised, and the defensive strategy to apply in such situations.
“The way companies treat digital identity can either lead to business and customer enablement, or significant financial loss. With that in mind, business and IT teams need to work together in creating a strategic identity governance road map built around zero trust, a layered approach to identity (identity in depth), and automated identity processes.”
– Shinesa Cambric
Pillars of Identity
When we think about the components of identity management, we can use a Maturity Model to give us an evidence-based instrument for recording current capabilities and defining our desired future state. This assessment gives a relatively quick overview of the current IAM situation and the critical areas that require attention. A maturity assessment should look across the four Pillars of Identity for a thorough review of the organization’s capabilities. These pillars are:
1. Identity Governance
This is one of the overarching pillars where the governance committee meets regularly and has the authority to prioritize, develop, implement, and monitor IAM-related tasks and goals. The team has control over the repository of identities in an organization and has information on what these identities are doing.
2. Access Management
This section comprises the provisioning/deprovisioning and transitioning access policies and to check what access has been granted. Adaptive access enables organizations to better address access-related risks while improving user experience.
3. Authentication
As the name suggests, here you are managing authentication through single sign-on or zero trust methodologies. Current trends include password-less authentication or making sure that passwords are not being reused in the system.
4. Privileged Access
This section considers policies to be managed to store/ vault privileged accounts or admin accounts. Emphasis is made to verify if the accounts are appropriately locked down or checked out by a user upon request and for a short duration.
Shift to a Cloud Identity Mindset
With the Cloud, Identity replaces network hardware as the new security perimeter. Identity becomes the foundational component of cloud security programs. Each organization has its own systems to manage and needs to tailor its approach to Identity Management to its risk management objectives. Thorough planning is required to get it right.
Identity has evolved beyond managing access for users, it also includes controls for IoT (Internet of Things), APIs, BOTs, IP addresses, and more. All of these endpoints only increase the attack surface, adding new entry points where an attacker could get into a system. As the complexity of the environment goes up, so does the risk of a breach. Cyber attackers have the advantage because they only need to exploit a single vulnerability while our InfoSec teams have the much more difficult task of mitigating all vulnerabilities. Part of InfoSec’s objective is to make it difficult for hackers to acquire and use an exploit. Achieving this goal begins with asking the following questions:
- Who or what is on the other side of a connection?
- Where is the connection coming from? Where are you sending it to?
- What is the access required and which accounts (privileged and admin accounts) have access and for how long?
- When should connectivity be taking place?
- Are we monitoring for alerts or anomalies if there are any? What is the mitigation plan in each scenario?
In thinking about these scenarios, we can better understand our level of risk and what security measures to put in place to mitigate the threat of an attack.
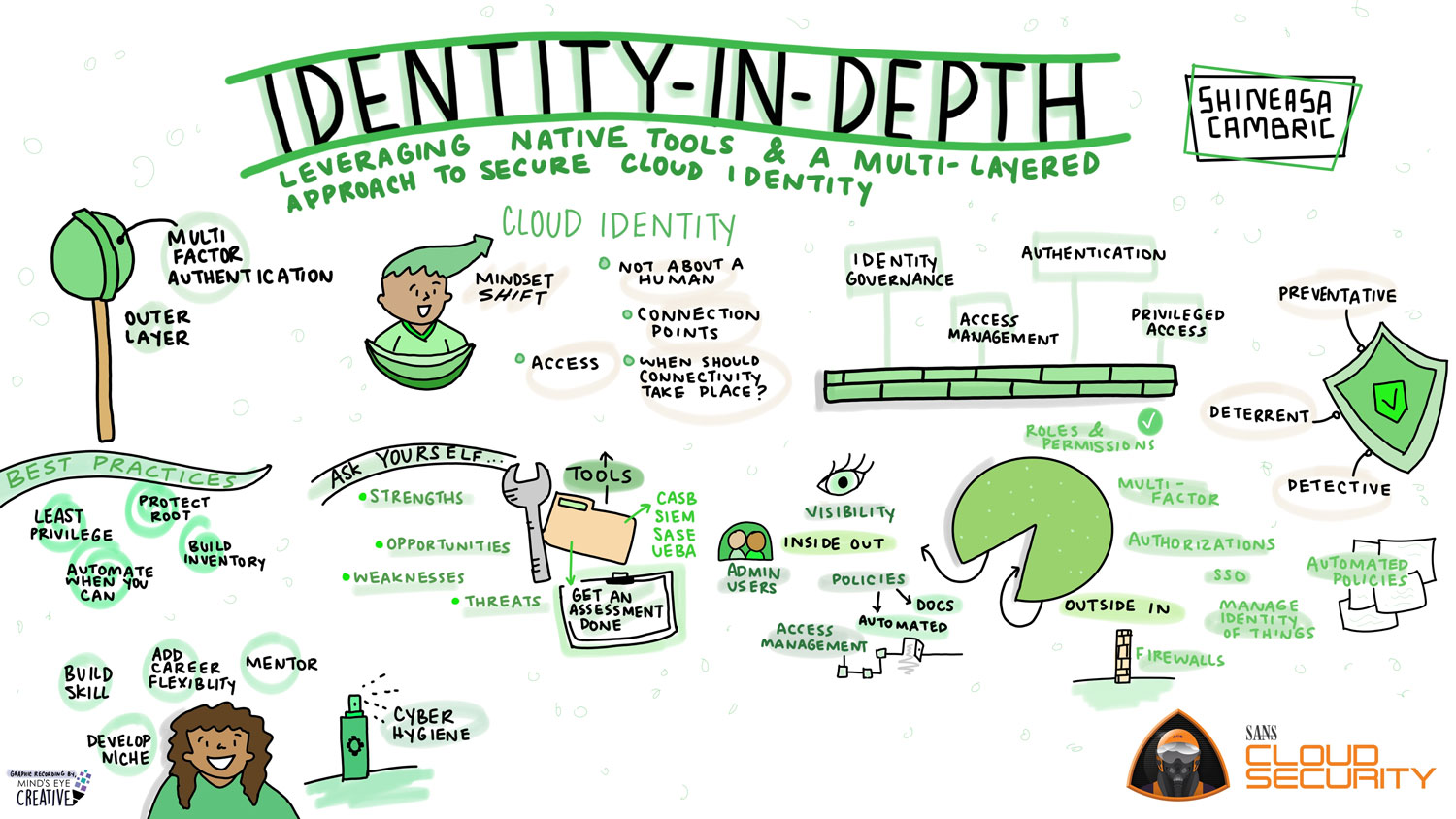
Layering on Identity-in-Depth
In simple terms, Defense in Depth is an approach to cybersecurity where a series of defensive mechanisms are layered in order to protect sensitive data and information. If one security mechanism fails, another is there to help thwart an attack. To build a strong defense in depth, we must incorporate identity management capabilities throughout the cloud environments. With multiple security layers, the likelihood of a successful cyberattack decreases. A key component of Defense in Depth is incorporating identity management capabilities using both Inside-out and Outside-In approaches.
Outside In: In order to implement a secure layer of defense within your organization, the following factors need to be applied in a collective manner.
- Zero Trust Architecture: Implement a strategy for zero trust architecture
- Single Sign On
- Multi Factor Architecture
- Authorization: Check what are the authorizations that are being assigned, for how long and what is the deprovisioning policy that is followed
- Manage Identity of Things: Include a repository of identities that is being used within the organization
- Segmentation / Virtual Firewalls: Include a tracker regarding which IP addresses must be allowed.
- Roles and permissions: Create a policy using RBAC approach and monitor the roles on a timely basis
- Configuration policies: Create automated policies to check the security posture of an organization. Make sure that when services are being deployed, the security posture that is maintained isn’t deflected.
Inside out: Insider threats are as valid as outsider attacks. In order to secure a strong perimeter of defense, a few best practices should be adhered to.
- Visibility: Implement a tool that acts as a single pane of glass for user entitlement reviews. Integrate the system with the connectors and have the latest copy of the identity inventory. Monitor and manage behavior analytics that track any anomalies that have been triggered within the system. Prepare a plan to track the access managed by APIs and what are the policies that are applied to API access management.
- Admin Users: Manage a monitoring plan to secure and track who has access, on what system, and if it is managed appropriately. Log or record instances when an admin account is being used on a server and monitor the activity.
- Policies: Employ formalized access policies and asset identification. Automate policies to detect any anomalies or automatically rollback if authentication is not maintained.
- Access Management: Excessive employee access is one of the fastest-growing risks to the protection of critical enterprise data. Utilize least privilege security models to tailor access based on what the user needs and eliminate entitlement creep.
In closing, in order to fully recognize the benefits of the Cloud, an organization must proactively reduce the risk of a successful cyber attack. The complexity of systems and the ever-changing nature of threats require the development of an expert and forward-thinking cybersecurity strategy. Identity and Access Management solutions are key components of the security framework as are disciplined processes to improve access control, such as: verifying the identity of every user, validating every device, limiting access and privileges, as well as analyzing user behavior. Each layer of security reduces the chance of a successful attack, which is why Identity in Depth is critical to protecting the organization.
This article was written by Prajna Priyadarshini, Cyber Security Analyst at Idenhaus Consulting.
To receive the IAM Strategy and Cybersecurity articles in your inbox every two weeks (Tuesdays 8 PM EST), subscribe to our Identity Management biweekly and/or our Healthcare Cybersecurity and IAM Digest.
Follow @Idenhaus on Twitter and subscribe to our YouTube channel.

By going to work quickly to solve the most challenging cybersecurity and identity management problems, Idenhaus takes the pain out of securing corporate information and assets for companies that aspire to maximize their potential in this digital age. Click here to contact us






