
A distributed cyber attack occurs when a hacker tries to disrupt services and make key resources unavailable, such as a website or online application. An attack can have a single point of origin (also called Denial of Service, or DOS) or it can be perpetrated by a group of hackers (Distributed Denial of Service, or DDoS). Distributed attacks flood the victim’s IT systems with malicious requests that prevent the systems from receiving any new information. According to the United States Computer Emergency Readiness Team (US-CERT), the symptoms of a distributed attack are:
- Unusually slow network performance
- Unavailability of a particular website
- Inability to access any website
As an analogy to understand what a distributed attack is: Imagine a pizza place, a person calls and keeps the staff member on hold, or takes a lot of time to place an order, and then hangs up without confirming the order and repeats this process a number of times. This disrupts the service and prevents any legitimate customers from placing an actual order, causing the pizza place to lose business and bring sales down for the day. A group of people calling the pizza place repeatedly without ever placing an order is similar to a Distributed Denial of Service (DDOS) attack.
[feature_box style=”10″ only_advanced=”There%20are%20no%20title%20options%20for%20the%20choosen%20style” alignment=”center”]
Before you continue reading, how about following us on LinkedIn?
[/feature_box]
In a DDOS attack, the victim is flooded with incoming traffic from multiple sources. There is no way to determine which traffic is legitimate and which is not so it’s hard for the victim to block the attack. There are a number of tools and techniques that are used to carry out a DDOS attack. Some of the attackers employ the use of a botnet, which is a network of machines infected with malware that obey a single device. Botnets are generally used to overflow a machine with packets of malware data that use up the bandwidth.
The Layer 7 DDOS attack, or Application Layer attack, is particularly damaging because it consumes server resources and network resources. It targets the Open Systems Interconnection (OSI) layer, where web pages are generated on the server in response to HTTP requests. This attack will prevent the services on the web page from loading, and bring the victim’s website to a complete halt.
Two other common types of attacks are:
- Volumetric attack – the attacker attempts to occupy all bandwidth between the victim and the rest of the internet.
- Protocol attack – the attacker denies service by consuming the entire capacity of the victim’s traffic and transportation layers of a connection. E.g. SYN flood
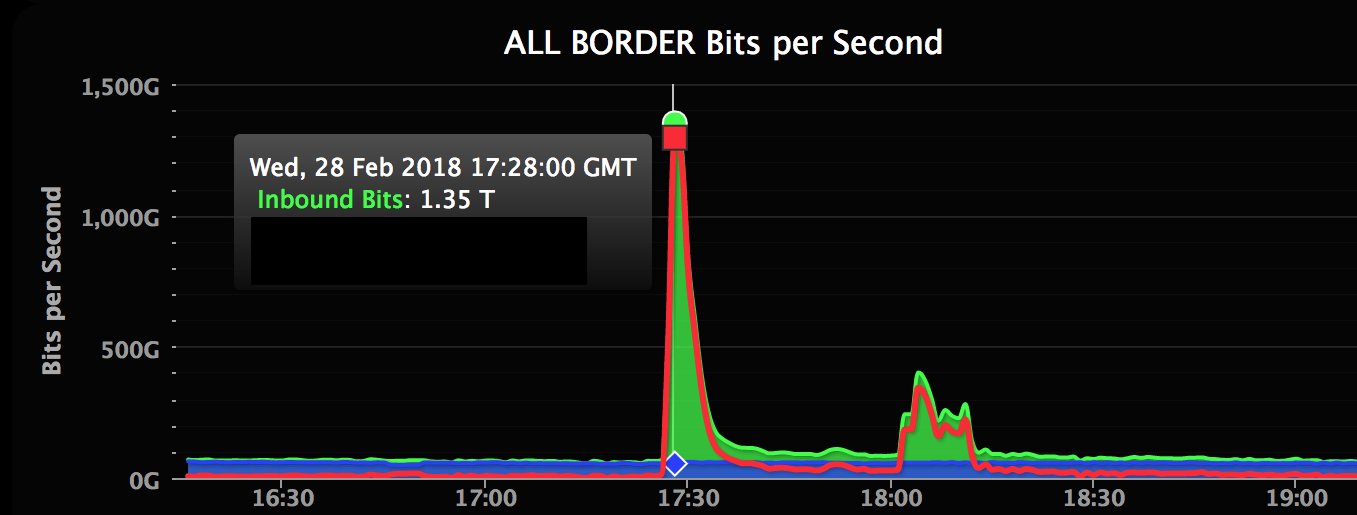
One of the largest distributed cyber attacks in the recent past involved Github getting hit by an attack of 1.35 terabits per second. This is the second-largest bandwidth DDOS attack recorded to date. According to the GitHub team, the attackers targeted a distributed memory system known for high performance and demand and tried to amplify the traffic columns that were being fired. The result was a huge influx of traffic that crashed the GitHub site, which was down for almost 5 minutes. The image below shows the high volume of traffic during the attack.
Protecting an organization from a distributed attack is a difficult task that begins with a thorough cybersecurity assessment of your IT environment. After determining the vulnerabilities in your organization, the next essential element is developing your mitigation plan. A mitigation plan for distributed cyber attacks should include the following:
- Configure firewalls and routers
This helps prevent malicious traffic from entering your internal network. Make sure to regularly update your routers and firewalls with the latest security patches. - Secure your Internet of Things (IoT) devices
IoT devices are easily exploitable. Consider these your most vulnerable devices and ensure your devices are secured with trusted (and up-to-date) security software. - IPS-based prevention
Intrusion Prevention Systems (IPS) are effective if they can detect and block DoS attacks by analyzing the network packet and distinguishing it from a legitimate network packet. An ASIC-based IPS method is one of the ways to achieve this. - Application front end hardware
This is intelligent hardware that can analyze the network traffic and identify it as priority or dangerous. It is placed on the network before traffic reaches the servers and can be used conjunction with routers and switches.
Learn more about how you can protect your organization with a Cybersecurity Assessment by downloading our newest case study.
This article was written by Prajna Priyadarshini, Cybersecurity Analyst at Idenhaus Consulting.
Follow @Idenhaus on Twitter and subscribe to our Identity Management biweekly or our healthcare IT biweekly newsletter.
Idenhaus is honored to be featured in the Top 10 Identity Governance and Administration Consulting/Service Companies of 2019.
By going to work quickly to solve the most challenging cybersecurity and identity management problems, Idenhaus takes the pain out of securing corporate information and assets for companies that aspire to maximize their potential in this digital age. Click here to contact us







