Mastering Identity Management: Keep Your Friends Close and Your Stakeholders Closer
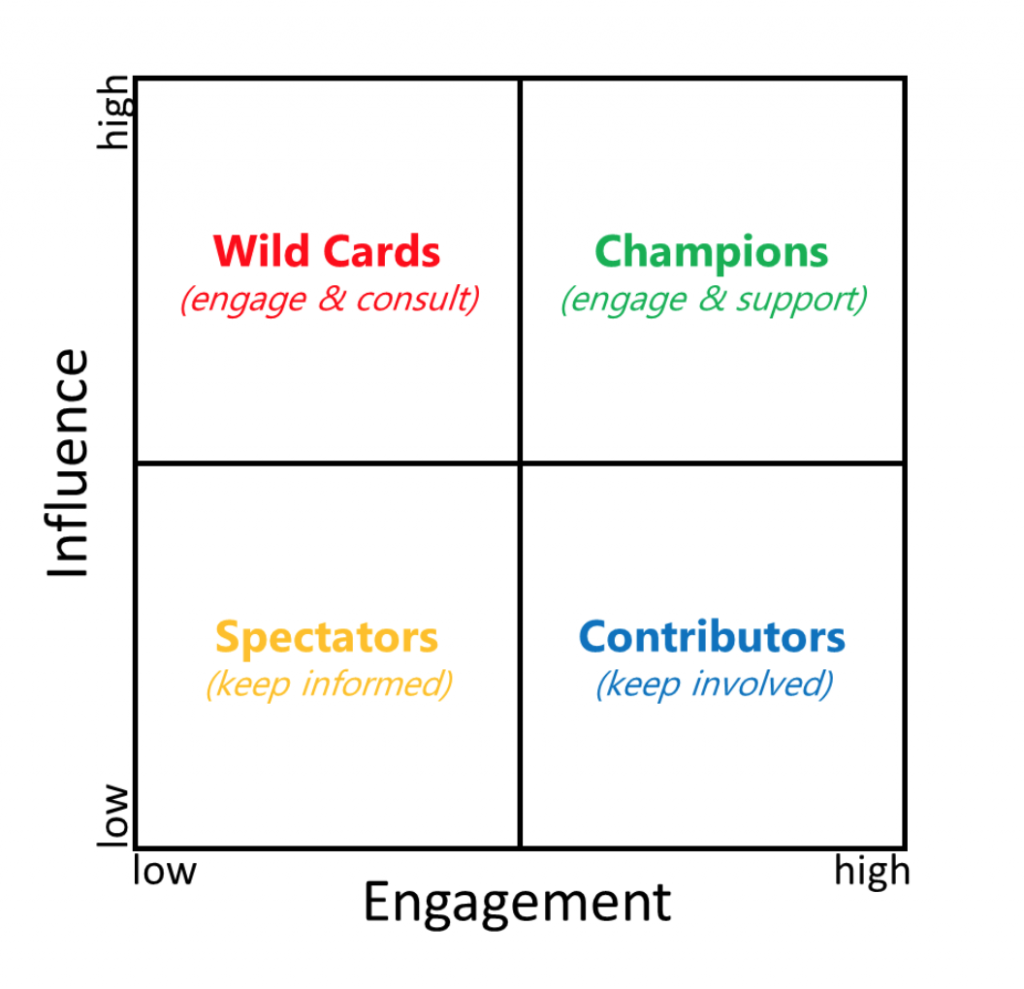
Stakeholders are an important asset and are critical to the success of your Identity and Access Management program. Few IT projects have such far-reaching scope as Identity Management (IAM) engagements, touching stakeholders across all business domains. The breadth of IAM’s reach is also its downfall – with new requirements springing up like mushrooms after a […]
Mastering Identity Management: Keep Your Friends Close and Your Stakeholders Closer Read More »