9 Informative Identity Management Articles, October 2017
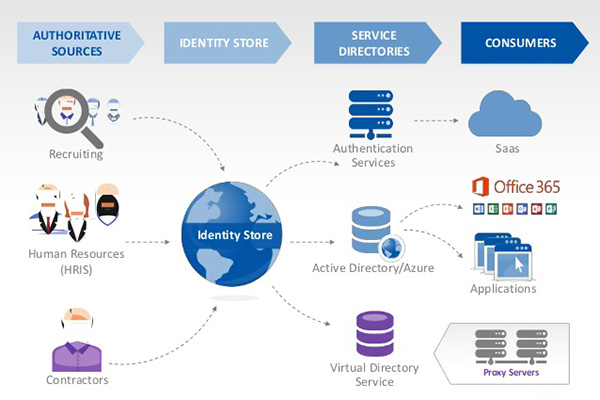
Stay highly informed with our biweekly Identity Management & Cybersecurity news digest. We curate the best IAM & Cyber security articles to help you navigate the ever-changing IT landscape. Subscribe to our biweekly newsletter here. Here are 9 IAM & Cybersecurity articles to help ensure your Halloween is full of treats and not tricks. How To Design, Choose And Implement The Right […]
9 Informative Identity Management Articles, October 2017 Read More »