8 Benefits of an Identity & Access Management Roadmap
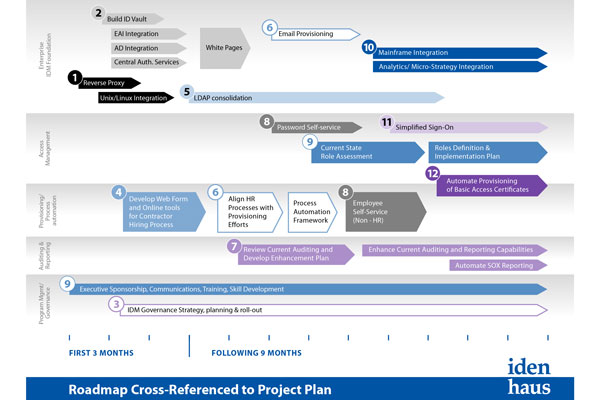
Creating an Identity & Access Management (IAM) roadmap is an important first step in helping your organization reap the full benefits of its IAM investment, as well as driving organizational understanding and support. While many organizations do a good job of laying out their technical requirements, too often they fail to link their implementations to […]
8 Benefits of an Identity & Access Management Roadmap Read More »