3 Most Popular Identity Management Articles
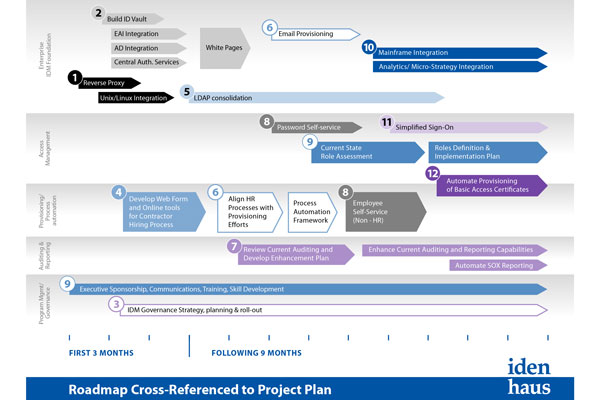
Identity Management is often approached as a pure technology play, which is why more than half of all IAM projects fail the first time. All too often companies select a technology and begin implementation. However, the reality is that a successful IAM program touches many areas of the business and involves buy-in from both technical and business […]
3 Most Popular Identity Management Articles Read More »